Some online tools are invisible helpers. You switch them on, the web feels calmer, and your data stops leaking everywhere. A VPN is one of those tools. But what is a VPN, exactly? And how does it pull off that cloak-and-tunnel magic without breaking your internet?
Whether you’re comparing features for work, studying privacy, or trying to keep streaming and gaming smooth, this guide explains the essentials in plain English. We’ll also Compare VPN Services concepts and alternatives so you can spot what matters and what’s just marketing fluff.
Explore more private browsing guides on Compare VPN Services
What Is a VPN?
VPN stands for Virtual Private Network. It is a secure, encrypted connection between your device and a remote server. When the VPN is on, your internet traffic goes through this encrypted tunnel first, then out to the open web. Websites and networks see the VPN server’s IP address, not yours. That improves privacy on public Wi-Fi, helps reduce tracking, and can provide a consistent experience across different networks.
At its core, the idea is always the same: a protected path that hides your IP and scrambles your data so observers cannot easily read or link your activity to you.
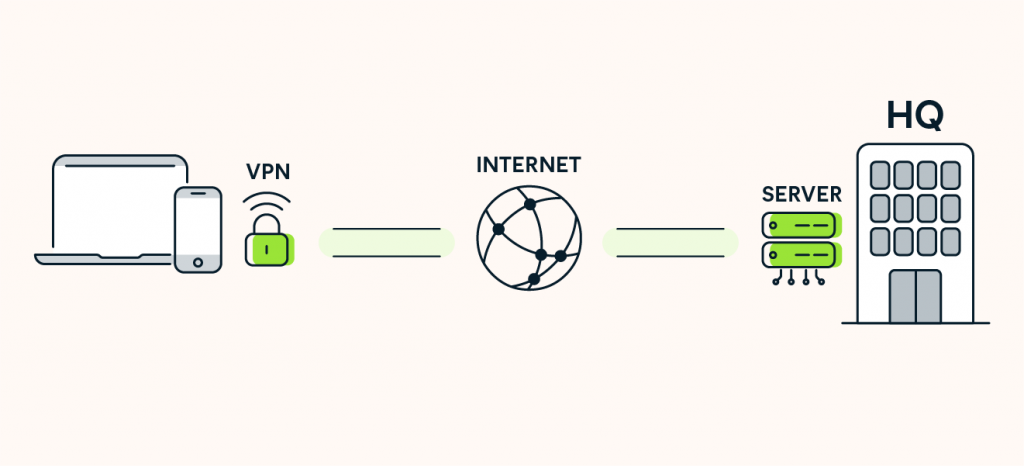
Why people use a VPN
- Privacy on public Wi-Fi. Coffee shops, airports, and hotels are crowded networks. A VPN blocks easy snooping of unencrypted data.
- IP masking. Sites and services see the VPN server’s IP, not your original one, which helps reduce profiling.
- Network consistency. A VPN can stabilize access when a local network is restrictive, such as campus or workplace guest networks.
- Work access. Businesses often use VPNs so employees can reach internal tools securely from outside the office.
- Less price steering. Masking your IP may reduce price discrimination that can occur by location. It does not guarantee lower prices, but it helps your research be more consistent.
See our privacy and security checklist on Compare VPN Services
How a VPN works under the hood
Understanding what is a VPN becomes easier when you break the connection into steps:
- Client starts the tunnel. You open a VPN app and pick a server location. The app is the “client.”
- Handshake and keys. The client and server authenticate each other and agree on cryptographic keys. This enables encryption.
- Routing. Your device sends internet traffic into the encrypted tunnel. The VPN server forwards it to the destination website or service.
- Reply path. Responses come back to the VPN server, then through the tunnel to your device.
- IP and DNS. The outside world sees the server’s IP. When set correctly, your DNS queries also travel through the tunnel to a resolver the provider controls or trusts, which helps prevent DNS leaks.
If any of those pieces are misconfigured, you lose benefits. For example, if DNS leaks outside the tunnel, websites can still learn where you’re going.
Key VPN protocols explained
Protocols are the blueprints for building the tunnel. The right one balances speed, security, and reliability.
- WireGuard. Modern, lean, and fast. Uses state-of-the-art cryptography with a small codebase that’s easier to audit. Great for mobile due to speedy reconnections.
- OpenVPN. Battle-tested and flexible. Runs over UDP for speed or TCP for reliability. Slightly heavier than WireGuard but widely supported.
- IKEv2/IPSec. Good at switching networks without dropping the tunnel, which is helpful on phones moving between Wi-Fi and cellular.
- L2TP/IPSec and PPTP. Older options. PPTP is considered obsolete for security. L2TP/IPSec is better than PPTP but largely replaced by the options above.
Encryption and authentication, in simple terms
- Encryption ciphers. Your data is scrambled with algorithms such as AES-GCM or ChaCha20-Poly1305. These ciphers make data unreadable to outsiders.
- Forward secrecy. Session keys change frequently. Even if a key were compromised, only a narrow slice of traffic would be at risk.
- Authentication. The server proves it is the real server, often with certificates. The client also authenticates, so strangers cannot hijack your session.
- Integrity checks. Message authentication codes help detect tampering.
A practical comparison: VPN vs alternatives
When you Compare VPN Services to other privacy tools, it’s easy to confuse roles. Here’s a quick map.
Table: VPN vs Proxy vs Tor vs Smart DNS
| Feature | VPN | Proxy | Tor | Smart DNS |
|---|---|---|---|---|
| Encrypts all device traffic | Yes | Usually no | Yes, within Tor browser/app | No |
| Masks IP address | Yes | Yes | Yes | No |
| App-wide protection | Yes | Often app-specific | Browser-only by default | DNS-only |
| Speed consistency | High with modern protocols | Medium | Lower due to multi-hop relays | High |
| Easiest for non-technical users | High | Medium | Medium | High |
| Main use case | Privacy + security + consistency | Lightweight IP masking | Strong anonymity research | Region-optimized DNS resolution |
Takeaway: A proxy hides your IP but usually leaves traffic unencrypted. Tor is powerful for anonymity but slower. Smart DNS is for DNS routing tweaks, not privacy. A VPN balances privacy, speed, and whole-device coverage.
Compare more privacy tools on Compare VPN Services
What a VPN can and cannot do
Can do
- Hide your IP address from websites and apps you use.
- Encrypt traffic between your device and the VPN server.
- Reduce exposure on insecure networks.
- Provide a more uniform online experience across networks.
Cannot do
- Make you invincible. If you log into accounts, those sites still know it’s you.
- Stop all tracking. Browser fingerprinting and cookies can still identify patterns.
- Replace antivirus or OS updates.
- Fix unsafe habits, like reusing passwords.
Understanding what is a VPN means setting the right expectations. It’s a strong layer, not a magic shield.
Do you need a VPN at home?
Many people ask: if my home Wi-Fi uses WPA2 or WPA3, do I still need a VPN?
- Home networks are safer than public ones, but your ISP can still see metadata like domains you visit unless you use encrypted DNS and HTTPS. A VPN hides this from your ISP by putting the server in the middle.
- Consistency across devices. If you move between home, office, and public Wi-Fi, keeping the VPN on creates predictable protection.
- Work or study requirements. Some organizations require a VPN for accessing resources.
The question is less “do I need it?” and more “when do I benefit from it?”
Mobile vs desktop: same tunnel, different realities
- Mobile reconnection matters. Phones switch networks frequently. Protocols like WireGuard and IKEv2 shine here because they re-establish tunnels quickly.
- Battery and background apps. VPN encryption uses resources, though modern phones handle it well. Good clients pause or limit background handshakes when idle.
- Split tunneling. You can choose which apps go through the VPN and which bypass it. Handy for local banking apps or streaming devices on your LAN.

The role of no-logs policies and audits
You’ll often see “no-logs” in marketing. Translated: the provider claims it does not keep records that could identify what you did online. Since this is a trust statement, independent security audits and transparent infrastructure details matter. When you Compare VPN Services, look for clear explanations of what is or isn’t logged, and whether third parties have tested those claims.
We’re not promoting any provider here. The principle is simple: strong technology plus verifiable transparency beats vague promises.
Kill switch, leak protection, and other core features
- Kill switch. If the VPN drops, the app blocks traffic until the tunnel is back. This prevents accidental exposure.
- DNS leak protection. Ensures your DNS goes through the tunnel.
- IPv6 handling. Either tunnels IPv6 safely or disables it to avoid leaks on networks that support IPv6.
- Multi-hop. Routes your traffic through two VPN servers in series. More privacy, some speed tradeoff.
- Obfuscation. Makes VPN traffic look like normal HTTPS to get around restrictive networks.
Performance: why speed varies
Speed depends on:
- Distance to server. Closer is usually faster.
- Protocol choice. WireGuard and modern OpenVPN settings often perform best.
- Server load and peering. Two servers in the same city can behave differently depending on their network paths.
- Device power. Older routers and phones may struggle with heavy encryption.
In 2026, VPN performance is generally strong on modern hardware, especially with WireGuard-based setups. Still, expect minor delays due to encryption and routing.
Privacy hygiene to pair with a VPN
Even the best tunnel benefits from good habits:
- Use a hardened browser. Clear cookies, limit invasive extensions, and consider private windows for research.
- Enable MFA. Add multi-factor authentication to key accounts.
- Update systems. Keep OS, apps, and firmware current.
- Strong passwords. Use a password manager and unique credentials per site.
- Encrypted DNS. Consider DNS-over-HTTPS or DNS-over-TLS even outside the VPN.
Comparison mini-table: Common VPN protocols at a glance
| Protocol | Speed | Security | Best for | Notes |
|---|---|---|---|---|
| WireGuard | Very high | Excellent | Everyday use, mobile | Fast handshakes, lean codebase |
| OpenVPN UDP | High | Excellent | Streaming, gaming | Lower latency than TCP |
| OpenVPN TCP | Medium | Excellent | Unstable networks | Better reliability than UDP |
| IKEv2/IPSec | High | Strong | Mobile roaming | Quick reconnections |
| L2TP/IPSec | Medium | Moderate | Legacy setups | Superseded by newer options |
| PPTP | High | Weak | Avoid | Obsolete for security needs |
Common mistakes to avoid
- Relying on a free proxy for security. Proxies usually do not encrypt traffic.
- Ignoring DNS leaks. Always test your setup after enabling the VPN.
- Assuming anonymity. A VPN is for privacy and security, not guaranteed anonymity.
- Forgetting split tunneling rules. Make sure sensitive apps are included in the tunnel.
- Leaving the kill switch off. It takes one outage to expose traffic.
Browse our setup guides and checklists on Compare VPN Services
Frequently Asked Questions
What Is a VPN and do I really need one at home?
A VPN is an encrypted tunnel between your device and a server that hides your IP and protects data in transit. At home, it adds privacy from your ISP and provides consistent protection across networks. Whether you need it depends on your risk tolerance and habits.
How does a VPN hide my IP address?
When the VPN is on, websites see the VPN server’s IP instead of yours. Your traffic exits to the internet from that server, not directly from your device.
Will a VPN slow my internet?
Some overhead is normal due to encryption and routing. With modern protocols like WireGuard and nearby servers, most users experience minor slowdowns that are barely noticeable for browsing and streaming.
Is a VPN the same as a proxy?
No. A proxy can mask your IP for a single app or connection but typically does not encrypt traffic. A VPN encrypts device-wide traffic by default.
Can a VPN make me anonymous?
No. It improves privacy and security, but sites you log into will still identify you. Browser fingerprinting and account activity can link sessions.
Is it legal to use a VPN?
In most countries, yes. The legality depends on where you live and what you do online. A VPN does not permit illegal activity.
What is split tunneling and should I use it?
Split tunneling lets you choose which apps use the VPN. It can improve performance for local apps, but be careful not to exclude sensitive ones.
What is a kill switch and why does it matter?
A kill switch blocks traffic if the VPN drops, preventing accidental exposure. It is essential for consistent privacy.
Which one protocol is best?
There isn’t a single best choice. WireGuard is fast and modern. OpenVPN is mature and flexible. IKEv2/IPSec is great for mobile roaming. Pick based on your needs.
Does it protect me from malware?
Not directly. Some apps include blockers for malicious domains, but you still need good device security, updates, and safe browsing habits.
The bottom line
If you started this article asking What Is a VPN, you now know it is a secure, encrypted tunnel that hides your IP, protects data in transit, and helps keep your online activity private. It is not a cure-all, but paired with smart habits and modern protocols, it’s one of the most practical privacy tools you can use.
When you Compare VPN Services or evaluate features, focus on protocol support, leak protection, audits, and usability. Those fundamentals will matter far more than buzzwords.
Keep learning with our VPN fundamentals hub on Compare VPN Services

